
"Online Fraudster Robbed U.S. Merchants of $3 Billion in 2006"
"E-Commerce Fraudsters' Haul May Reach $3.6 B in 2007"
"E-Commerce Fraud on the Rise!"
These are some of the headlines that hit several online e-commerce journals such as e-Marketers.com, PCMAG.com, E-Commerce Times.com, Examiner.com, etcetera on Nov 2007. These articles reported the survey undertaken by CyberSource, a company that has been studying e-commerce fraud for 9 and more years. Report also showed that "fraudulent individuals are increasingly targeting businesses directly for large amounts of data rather than attacking one customer at a time..."
This is a clear warning sign to every individual -- It's time to double safeguard our personal & financial data!
There are many ways/ tips to safeguard your personal & financial data that you can easily find from the Web sites. Here are some simple reminders:
a) Password/ Encryption
- Create passwords to protect your private information.
- Avoid using 1 password for all accounts that you create.
- Avoid using IC no, birth date, phone no, car registration no, and other familiar no that can be easily identified as your passwords.
- Use "Alpha-Numeric" passwords.
- Better still, use encryption to protect important files or data.

b) Anti-Virus/ Anti-Spyware Software
- Keep an up-to-date, working anti-virus/ anti-spyware software running on your PC all the time.
- Scan your computer frequently for viruses, bugs, spyware, adware, trojans as these malicious intruders may attempt to disseminate your information or destroy it.
- Suggested free anti-virus/ anti-spyware software are AVG Free 8.0 and Spybot.

- Never ever visit suspicious Web sites. Web sites that claim they are giving out huge prizes without obligations are one example of suspicious Web sites that may lure you into giving out your personal & financial data, and thus should be avoided.

- Do not response to any e-mails or messages that ask you to re-enter your password, personal & financial data because they may be a scam. If worried, you should call that particular organization to check out and reconfirm such thing.

- Never check the "Remember Me" option upon login if you are using computers in cyber cafe or any public computer terminal.
- Make sure that all transactions are done thru a Secure URL (e.g. https:// the https:// representing a secure line) A Secure URL can be determined by the following characteristics:
- URL begins with https:// as opposed to http://
- Padlock icons will appear in your browser indicating a secure connection
- For some browsers (e.g. Mozilla Firefox) the address bar will be highlighted (usually yellow in color) to indicate it is a Secure URL.

- Try to always transact at home. If forced to go to a cyber cafe, try to check for keyloggers or anything that might be an attempt to steal your data. Even a mirror on the wall that allows people to see what you are typing is considered dangerous.
- Before continuing a transaction, you may want to verify whether the particular Web site is genuine or a phish. Check out Mr. Hen's My E-Commerce Blog regarding PhishTank.
*By Shu*



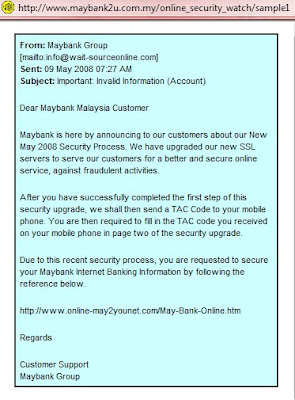















 This is the attack that specifically aim to do harm, it also known as premeditated attack. They can be further broken down into attacks caused by malicious code and those caused by intentional misrepresentation. Malicious code, on the other hand, is at the root of so-called "crackings" and "hackings" - notable examples of which include computer viruses, data theft, and Denial of Service (DOS) attacks.
This is the attack that specifically aim to do harm, it also known as premeditated attack. They can be further broken down into attacks caused by malicious code and those caused by intentional misrepresentation. Malicious code, on the other hand, is at the root of so-called "crackings" and "hackings" - notable examples of which include computer viruses, data theft, and Denial of Service (DOS) attacks.











